In this tutorial, we will deploy a production-ready Odoo 14 instance. Install it from GitHub source on a brand new DigitalOcean Droplet Ubuntu 20.04 (LTS) x64. What we will do:
- Going through DigitalOcean registration
- Installing all the Ubuntu 20.4 requirements necessary to install Odoo from the source
- Using Pyenv to prepare our server for multiple python versions and virtualenvs in case you want to host other versions of Odoo
- Creating
odoouser and making Odoo run as a service - Install Let's Encrypt SSL Certificate
- Making Odoo multiprocess and using Nginx as a reverse proxy
- Basic security with ufw
DigitalOcean offers you 100€ credit to use in 6 months since you can create machines and destroy them quickly it's a great place to experiment with Odoo installs or to choose it as your production server!
Creating a DigitalOcean account
First of all, go to DigitalOcean and create an account using the link

Create your credentials, validate your email and follow the steps until you arrive on that page
Here it can get a bit confusing because most of the links direct you to the DigitalOcean platform but we want the regular dashboard so click on Explore our control panel
When on the Control Panel click on Get Started with a Droplet or Create / Droplet to arrive on this screen
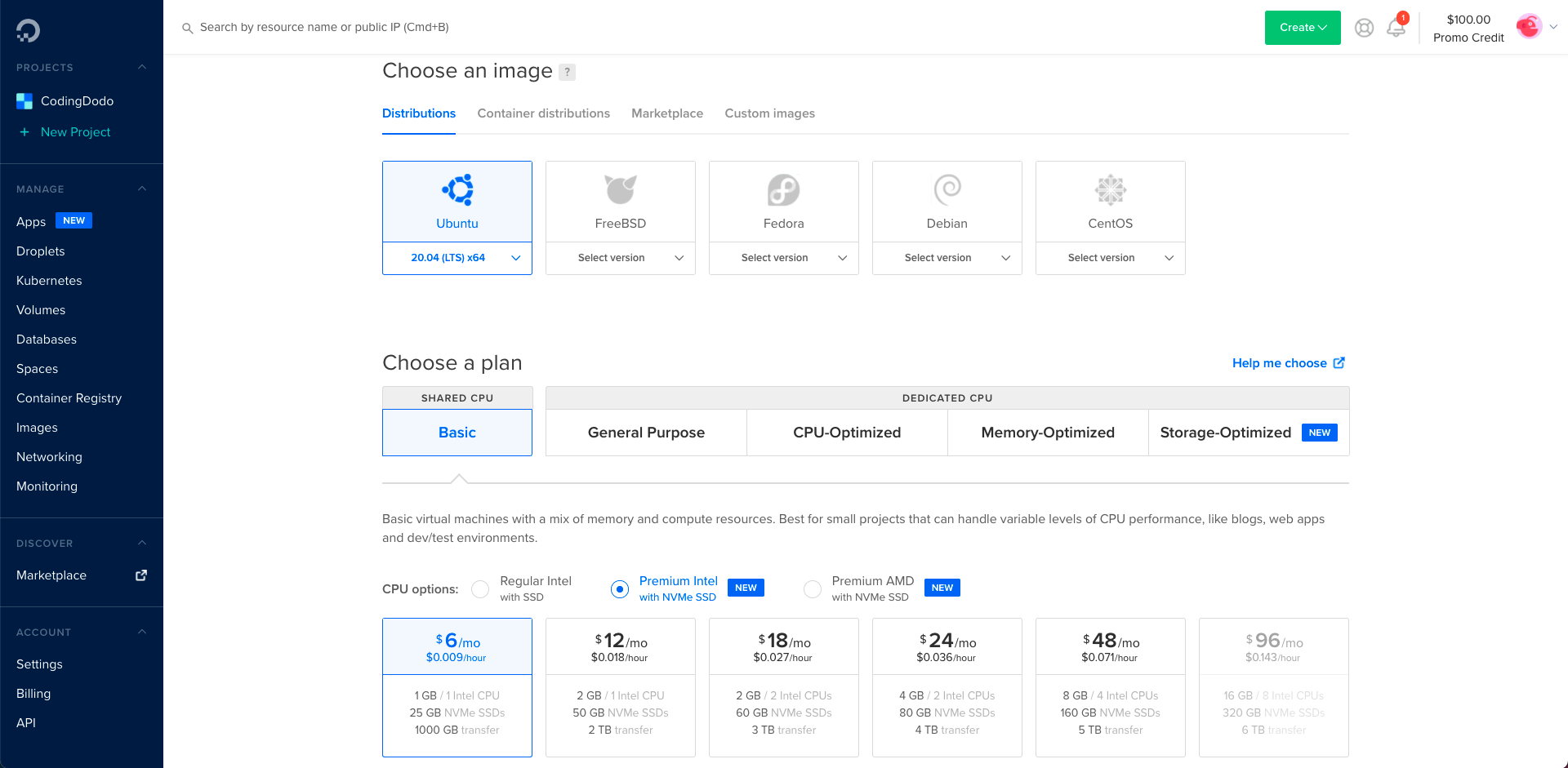
Choose Ubuntu 20.04 and choose the right machine based on your needs. Remember that you are only billed for the time that the machine is up so you can choose a good machine and destroy it later. Choose at least 2 CPUs or everything will feel very slow.
Scrolling down you will see a space to add your ssh-key
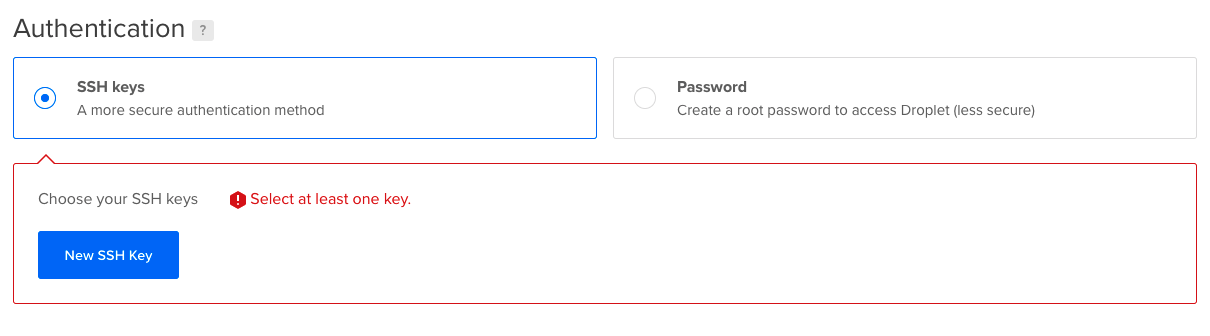
Adding SSH Key
If you don't have an SSH Key yet you have to generate it with the command. You probably already have an id_rsa.pub file in your .ssh folder. For this example, we will create a new SSH key that will be used to connect to our DigitalOcean Droplets. Feel free to skip that part or read it to create your first key or handle multiple ssh keys.
ssh-keygen -C "[email protected]"When prompted for the name of the file we choose that
/Users/codingdodo/.ssh/id_rsa_codingdodoShow the content of the newly generated key:
cat ~/.ssh/id_rsa_codingdodo.pubOn DigitalOcean, click on New SSH Key and copy/paste the content printed out. Scroll down more and click on Create Droplet. It will take a minute then your Droplet will be ready
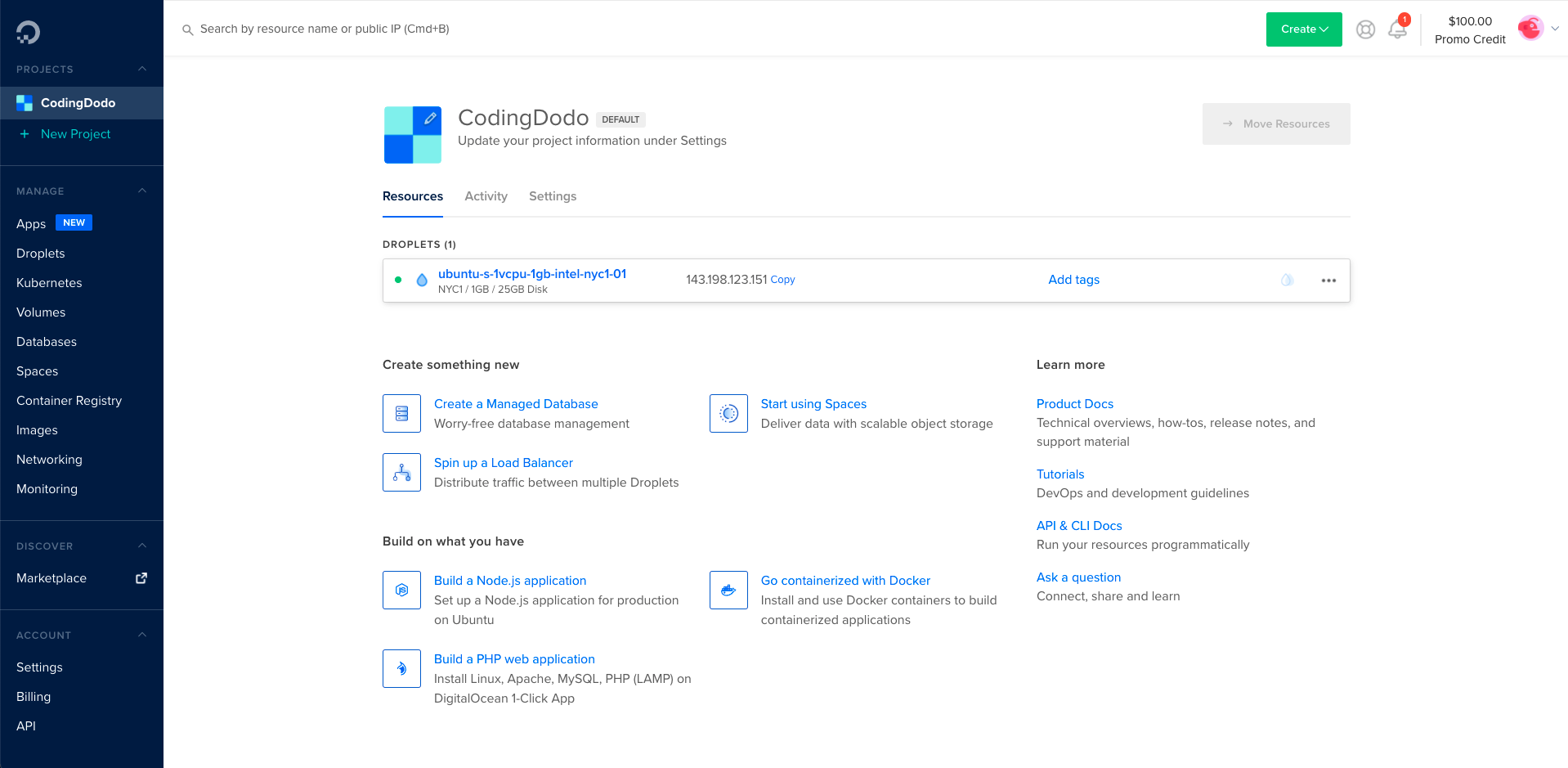
Copy the IP Address, we will add it to our SSH config file to make things easier for us. If you handle multiple SSH Keys this is a nice way to handle with which SSH Key you connect to each server.
vim ~/.ssh/configAdd this section with your IP address and the name of the public key you created.
Host testingdodo
Hostname 143.198.123.151
User root
IdentityFile ~/.ssh/id_rsa_codingdodo
IdentitiesOnly yesWe name our Host testingdodo so in our shell, we can type this shortcut to ssh into the machine.
ssh testingdodoAnd answer yes to the security prompt, and you will be logged in
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-51-generic x86_64)
...
root@ubuntu-s-1vcpu-1gb-intel-nyc1-01:~#Ubuntu 20.4 Prerequisites
On a new machine, I have the habit of updating the packages first before beginning installing everything. We start by updating our packages
apt updateThen we upgrade the installed packages.
apt upgrade -yIf you run into a message saying that the sshd_config has been modified:
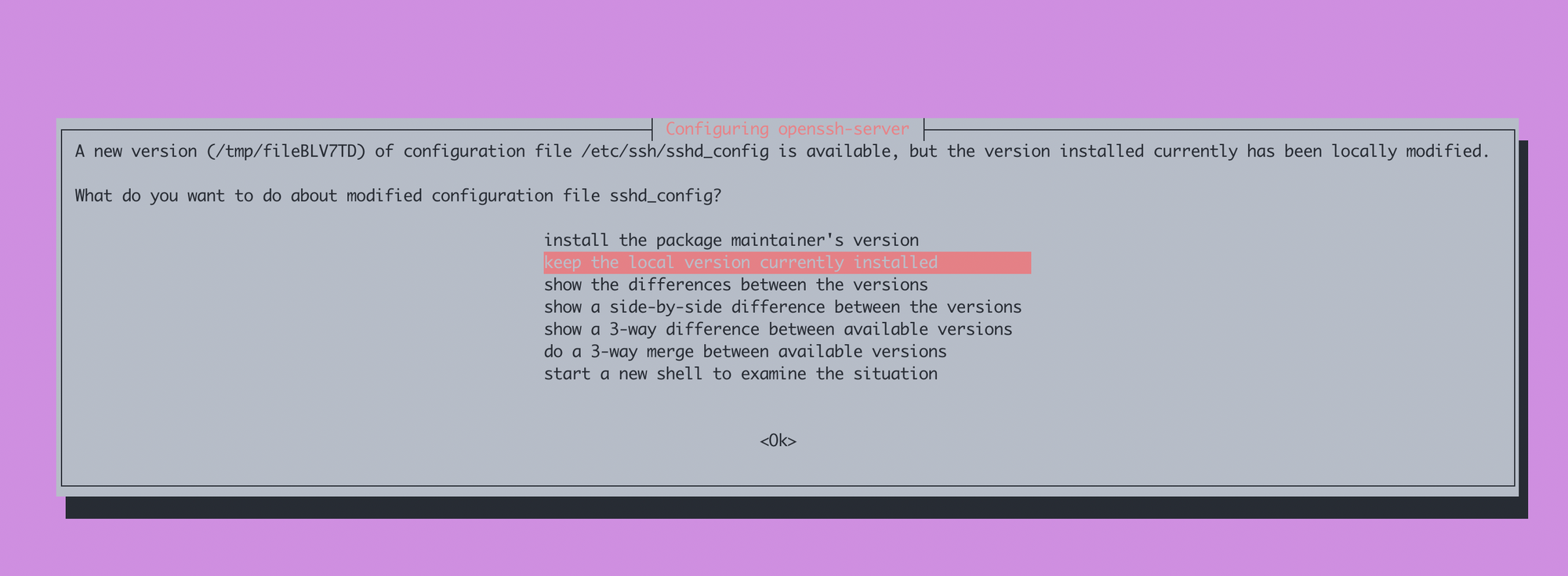
Choose to keep the local version currently installed.
Installing PostgreSQL
apt install postgresql postgresql-contrib -yWe will later create a Unix user named Odoo, so we will create a PostgreSQL user with the same name. If you would prefer a different name, remember to keep that consistency to make things easier when you come back later to your environment.
su - postgres
createuser --interactive -P odooWith the --interactive flag, PostgreSQL will ask us for a password and the privileges that will be given to our odoo PostgreSQL user.
Enter password for new role:
Enter it again:
Shall the new role be a superuser? (y/n) n
Shall the new role be allowed to create databases? (y/n) y
Shall the new role be allowed to create more new roles? (y/n) nNext, we will already create that database that will hold our Odoo 14 instance. In this example, it's gonna be named coding_dodo.
createdb -O odoo codingdodo_demo
exitThe -O flag represents the owner of the database, we choose odoo because it's the name of the PostgreSQL user we created just before
Wkhtmltopdf
Wkhtmltopdf is used by Odoo to generate documents and is a necessary evil. We will pull the deb of version 0.12.6-2 from Github and install it
wget https://github.com/wkhtmltopdf/packaging/releases/download/0.12.6-1/wkhtmltox_0.12.6-1.bionic_amd64.deb
apt install ./wkhtmltox_0.12.6-1.bionic_amd64.deb -yPython dev dependencies, git, Node, and other requirements
apt install -y build-essential libssl-dev zlib1g-dev libbz2-dev \
libreadline-dev libsqlite3-dev wget curl llvm libncurses5-dev libncursesw5-dev \
xz-utils tk-dev libffi-dev liblzma-dev python-openssl git libpq-dev libsasl2-dev libldap2-dev ccze node-lessCreating the Unix odoo user
useradd -m -U -r -s /bin/bash odoo-r indicate that it's a system account so useradd will not create a home directory for such a user. We want a folder so we use -m-U create a group and -s specify the shell that will be used.
Or if you don't want to have /home/odoo created to hold your odoo install and would prefer a different directory. This is an example that will create the home directory in /opt for example.
useradd -m -d /opt/odoo -U -r -s /bin/bash odoo-d [path] indicates we want to create a home but in different place.
Preparing a good Python environment with Pyenv
Log in as the odoo user
The pyenv will be installed as the odoo system user. That user is gonna run the odoo instance as a service later.
su - odooInstalling pyenv
curl https://pyenv.run | bashAdding python to the path
echo -e 'if shopt -q login_shell; then' \
'\n export PYENV_ROOT="$HOME/.pyenv"' \
'\n export PATH="$PYENV_ROOT/bin:$PATH"' \
'\n eval "$(pyenv init --path)"' \
'\nfi' >> ~/.bashrc
echo -e 'if [ -z "$BASH_VERSION" ]; then'\
'\n export PYENV_ROOT="$HOME/.pyenv"'\
'\n export PATH="$PYENV_ROOT/bin:$PATH"'\
'\n eval "$(pyenv init --path)"'\
'\nfi' >>~/.profile
Now log off and log-in again as odoo user
exit
su - odooInstalling python 3.9.2
pyenv install 3.9.2Depending on the CPU power you choose, it may take some time, but in the end, you should see:
Installed Python-3.9.2 to /home/odoo/.pyenv/versions/3.9.2As suggested by Jacob Christ in the comments, do a sanity check to see if pyenv can pickup python version in your environment by typing python --version you should see this.
odoo@ubuntu-s-4vcpu-8gb-amd-blr1-01:~$ python --version
pyenv: python: command not found
The `python' command exists in these Python versions:
3.9.2
Note: See 'pyenv help global' for tips on allowing both
python2 and python3 to be found.If you can't see the newly installed python you should check the pyenv documentation here to make it available in your path via a different method than what we did earlier.
Creating the virtualenv
pyenv virtualenv 3.9.2 odoo-14-envInstalling Odoo from GitHub source
Creating a folder for our custom addons (Optional)
mkdir /home/odoo/odoo-14-custom-addonsThis is the folder you will use to store your custom addons. Be careful if you add the custom addon patch to the --addons-path command-line argument and there are no valid addons inside, it will not work.
To make it work we will clone our own module inside that folder
cd /home/odoo/odoo-14-custom-addons
git clone https://github.com/Coding-Dodo/web_widget_markdown.git
cd ~/Pulling Odoo 14 and activating the virtualenv
We will pull Odoo version 14 with the -b flag for the branch and put it in a folder named odoo-14
git clone -b 14.0 --single-branch --depth 1 https://github.com/odoo/odoo.git odoo-14Since we created our virtualenv called odoo-14-env, we will "park" it in the odoo-14 folder we just created. With that every time we cd into this folder it will activate our virtualenv.
cd odoo-14
pyenv local odoo-14-envThe prompt should change and you should see (odoo-14-env) odoo@ubuntu-s-1vcpu-1gb-intel-nyc1-01
Do another sanity check by typing python --version you should now have that output:
odoo@ubuntu-s-4vcpu-8gb-amd-blr1-01:~/odoo-14$ python --version
Python 3.9.2Installing python dependencies
pip install --upgrade pip
pip install setuptools wheel
pip install -r requirements.txt -e .If you see any error please refer to the part "Python dev dependencies, git, Node and other requirements" and make sure you installed everything.
Launching Odoo for the first time to test and generate a config file
We will test launch Odoo with some command-line arguments that will be saved in our Odoo configuration file
./odoo-bin --database=codingdodo_demo --db_user=odoo --db_password=codingdodo -i base --without-demo=all --save -c /home/odoo/.odoorc_codingdodo_demo --stop-after-init
./odoo-bin --database=codingdodo_demo --db_user=odoo --db_password=codingdodo -i base --addons-path="/home/odoo/odoo-14/addons,/home/odoo/odoo-14-custom-addons" --without-demo=all --save -c /home/odoo/.odoorc_codingdodo_demo --stop-after-init
We directly typed the db name, user, and password and initialized it with the iflag. --without-demo=all is used because we are installing a production-ready environment. If you want demo data, omit that flag.
With the -c flag we told odoo where the config file will be /home/odoo/.odoorc_codingdodo_demo
The --save flag is used to save everything we just typed into the newly created config file.
(Optional) Updating config file admin_passwd with a random strong password:
If you want to quickly change the password inside your config file
sed -i "s/\badmin\b/$(openssl rand -base64 32 | awk '{print $1}')/g" /home/odoo/.odoorc_codingdodo_demoThis will replace the line admin_passwd = admin with a new password randomly generated via OpenSSL.
To check what the new admin_passwd is:
cat /home/odoo/.odoorc_codingdodo_demo | grep admin_passwd
...
admin_passwd = C4Yiyiez4CHMl5tsmRHVZHflfnITd3nF5oXh8l3ZPc8=Keep it somewhere safe because after running the instance it will be hashed.
Create the logs directory
We want our log files to be inside /var/log/odoo/ so we create that folder and give odoo user access to it.
exit
mkdir /var/log/odoo
touch /var/log/odoo/odoo-14.log
chown odoo: /var/log/odoo
chown -R odoo: /var/log/odoo/*log back as odoo and edit the config file
su - odoo
vim /home/odoo/.odoorc_codingdodo_demoModify the config file to reflect that change
logfile = /var/log/odoo/odoo-14.logOdoo as service
Log out of odoo user and create a service file
exit
vim /etc/systemd/system/odoo-14.serviceYou don't have to use vim to edit your file, but if you follow exactly the commands, to go into Insert mode press I, then copy that content via Ctrl + V (or Cmd + V)
[Unit]
Description=Odoo14
Requires=postgresql.service
After=network.target postgresql.service
[Service]
Type=simple
SyslogIdentifier=odoo-14
PermissionsStartOnly=true
User=odoo
Group=odoo
ExecStart=/home/odoo/.pyenv/versions/odoo-14-env/bin/python /home/odoo/odoo-14/odoo-bin -c /home/odoo/.odoorc_codingdodo_demo
StandardOutput=journal+console
[Install]
WantedBy=multi-user.targetIf you are using vim press :wq to save and exit the file.
Now we Reload the service.
systemctl daemon-reload
systemctl enable --now odoo-14Check status via systemctl status odoo-14 and you should see
systemctl status odoo-14
● odoo-14.service - Odoo14
Loaded: loaded (/etc/systemd/system/odoo-14.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2021-09-15 14:48:36 UTC; 5s ago
Main PID: 50819 (python)
Tasks: 4 (limit: 9513)
Memory: 59.8M
CGroup: /system.slice/odoo-14.service
└─50819 /home/odoo/.pyenv/versions/odoo-14-env/bin/python /home/odoo/odoo-14/odoo-bin -c /home/odoo/.odoorc_codingdodo_demo
Sep 15 14:48:36 ubuntu-s-4vcpu-8gb-amd-blr1-01 systemd[1]: Started Odoo14.Install Nginx and add SSL with Let's Encrypt
Installing Nginx
apt install nginx -yLet's Encrypt with Certbot
Certbot will be used to install our first certificate and to renew it every months
apt install certbot -yGenerate a new set of 2048 bit DH parameters by typing the following command:
sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048Let's Encrypt Nginx Snippet
Let's Encrypt need to do its acme-challenge to validate our domain name and creating the certificate with certbot. If we plan to install multiple instances / different domain names pointing to this server, it is a good habit to isolate the let's encrypt acme-challenge location to its custom snippet.
mkdir -p /var/lib/letsencrypt/.well-known
chgrp www-data /var/lib/letsencrypt
chmod g+s /var/lib/letsencryptWe create a Let's Encrypt snippet
vim /etc/nginx/snippets/letsencrypt.confWith this content
location ^~ /.well-known/acme-challenge/ {
allow all;
root /var/lib/letsencrypt/;
default_type "text/plain";
try_files $uri =404;
}SSL Conf Nginx Snippet
vim /etc/nginx/snippets/ssl.confCopy-paste that content
ssl_dhparam /etc/ssl/certs/dhparam.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384;
ssl_prefer_server_ciphers on;
ssl_stapling on;
ssl_stapling_verify on;
resolver 8.8.8.8 8.8.4.4 valid=300s;
resolver_timeout 30s;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
add_header X-Frame-Options SAMEORIGIN;
add_header X-Content-Type-Options nosniff;
Create A Record with your DNS Provider pointing to the Droplet IP
For the following parts, you must have a domain name that will point to your droplet or else the acme-challenge of Let's Encrypt will not pass and you will not have SSL so the final Nginx config file will not apply to you.
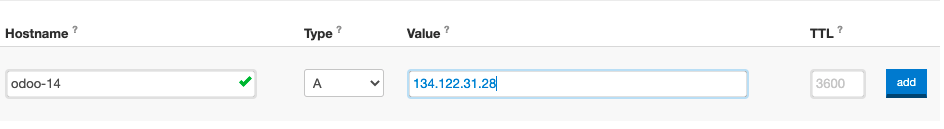
Here we created a subdomain of codingdodo.com with an A record pointing to our Droplet IP Value.
Our final address will be odoo-14.codingdodo.com
Installing the Let's Encrypt certificate
In case the Odoo service is still running.
service odoo-14 stopBasic Nginx Conf file to pass the Certbot acme-challenge
cd /etc/nginx/sites-available
vim odoo-14.codingdodo.comWe will first create a basic Nginx conf file to pass certbot acme-challenge:
upstream odoo_14 {
server 127.0.0.1:8069;
}
upstream odoochat_14 {
server 127.0.0.1:8072;
}
server {
listen 80;
listen [::]:80;
server_name odoo-14.codingdodo.com;
include snippets/letsencrypt.conf;
}Symlink your site declaration from site-available to site-enabled.
ln -s /etc/nginx/sites-available/odoo-14.codingdodo.com /etc/nginx/sites-enabled/odoo-14.codingdodo.comAlways test the config with nginx -t and if everything is okay we reload Nginx
service nginx reloadCertbot acme-challenge
It is now time to create our SSL certificate.
certbot certonly --agree-tos --email [email protected] --webroot -w /var/lib/letsencrypt/ -d odoo-14.codingdodo.comYou should see
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/odoo-14.codingdodo.com/fullchain.pemManaging Auto renew
Let's Encrypt already created a cron in the crontab but Nginx needs to reload to take into consideration the new certificate so we will edit this file
vim /etc/letsencrypt/cli.iniAnd add the line at the end.
deploy-hook = systemctl reload nginxTo test if our renew will work we can use the --dry-run flag to test it
certbot renew --dry-runFinal Nginx site conf for proxy mode multi workers
Now edit the odoo-14.codingdodo.com file again:
vim /etc/nginx/sites-available/odoo-14.codingdodo.comupstream odoo_14 {
server 127.0.0.1:8069;
}
upstream odoochat_14 {
server 127.0.0.1:8072;
}
server {
listen 80;
listen [::]:80;
server_name odoo-14.codingdodo.com;
include snippets/letsencrypt.conf;
location / {
return 301 https://odoo-14.codingdodo.com$request_uri;
}
}
server {
listen 443 ssl http2 default_server;
listen [::]:443;
server_name odoo-14.codingdodo.com ;
ssl_certificate /etc/letsencrypt/live/odoo-14.codingdodo.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/odoo-14.codingdodo.com/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/odoo-14.codingdodo.com/chain.pem;
include snippets/ssl.conf;
include snippets/letsencrypt.conf;
proxy_buffers 16 64k;
proxy_buffer_size 128k;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Odoo-dbfilter "codingdodo_demo";
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503 http_504;
location / {
proxy_pass http://odoo_14;
}
location /longpolling {
proxy_pass http://odoochat_14;
}
location ~* /web/static/ {
proxy_cache_valid 200 60m;
proxy_buffering on;
expires 864000;
proxy_pass http://odoo_14;
}
location ~* /website/image/ir.attachment/ {
proxy_cache_valid 200 60m;
proxy_buffering on;
expires 864000;
proxy_pass http://odoo_14;
}
gzip_types text/css text/less text/plain text/xml application/xml application/json application/javascript;
gzip on;
}
Use nginx -t to test the new config, you should see:
root@ubuntu-s-4vcpu-8gb-amd-blr1-01:/etc/nginx/sites-available# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successfulNow you can reload nginx.
service nginx reloadUpdating the Odoo config file
vim /home/odoo/.odoorc_codingdodo_demoNow that we have our reverse proxy we need to modify/add these lines
proxy_mode = True
workers = 4
max_cron_threads = 1
limit_memory_hard = 2684354560
limit_memory_soft = 2147483648
limit_request = 8192
limit_time_cpu = 600
limit_time_real = 1200The number of workers depends on the RAM and CPU you choose during the creation of your droplet. Refer to this official documentation to calculate the appropriate number of workers.
- Server with 2 CPU, 4 Thread
- 30 concurrent users
- 30 users / 6 = 5 <- theorical number of worker needed
- (2 * 2) + 1 = 5 <- theorical maximal number of worker
- We’ll use 4 workers + 1 for cron.
- RAM = 9 * ((0.8*150) + (0.2*1024)) ~= 3Go RAM for Odoo
Restart Odoo and see logs
service odoo-14 restartGo to https://odoo-14.codingdodo.com and in the meantime on the server check the logs
tail -f /var/log/odoo/odoo-14.log | cczeIn your browser access your domain name, you should see the login screen :
Setting the Firewall
Let's add some security!
ufw app listIf you followed this guide it should show you :
Available applications:
Nginx Full
Nginx HTTP
Nginx HTTPS
OpenSSHFirst, we secure ssh connection
ufw allow OpenSSHNow if you have installed Nginx with an SSL certificate
ufw allow 'Nginx Full'
ufw enableThe last line will ask you to confirm, enter y
Command may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startupCreate a sudo user for day to day actions
adduser codingdodoAnswer the prompt questions:
Changing the user information for codingdodo
Enter the new value, or press ENTER for the default
Full Name []: CodingDodo
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] YNow we update the rights for that user.
usermod -aG sudo codingdodorsync --archive --chown=codingdodo:codingdodo ~/.ssh /home/codingdodoWith DigitalOcean we already uploaded our ssh-key to the authorized_keys of the root so we are using Rsync to copy the folder with a new owner.
Wrapping up
This is the final Odoo config file
[options]
addons_path = /home/odoo/odoo-14/addons,/home/odoo/odoo-14-custom-addons
admin_passwd = $pbkdf2-sha512$25000$TwkBoDRGqBUi5LyXMiaE8A$SUyyCVfU1jk0YqiuTbHqVNmT31jw33fyh6tLMkA6t6lLSKpbnutYuQ.dVwQ2wIgWs2hf1OQmhNcHR9ofqGtSFg
csv_internal_sep = ,
data_dir = /home/odoo/.local/share/Odoo
db_host = False
db_maxconn = 64
db_name = codingdodo_demo
db_password = codingdodo
db_port = False
db_sslmode = prefer
db_template = template0
db_user = odoo
dbfilter =
demo = {}
email_from = False
geoip_database = /usr/share/GeoIP/GeoLite2-City.mmdb
http_enable = True
http_interface =
http_port = 8069
import_partial =
limit_memory_hard = 2684354560
limit_memory_soft = 2147483648
limit_request = 8192
limit_time_cpu = 60
limit_time_real = 120
limit_time_real_cron = -1
list_db = False
log_db = False
log_db_level = warning
log_handler = :INFO
log_level = info
logfile = /var/log/odoo/odoo-14.log
longpolling_port = 8072
max_cron_threads = 2
osv_memory_age_limit = False
osv_memory_count_limit = False
pg_path =
pidfile =
proxy_mode = True
reportgz = False
screencasts =
screenshots = /tmp/odoo_tests
server_wide_modules = base,web
smtp_password = False
smtp_port = 25
smtp_server = localhost
smtp_ssl = False
smtp_user = False
syslog = False
test_enable = False
test_file =
test_tags = None
transient_age_limit = 1.0
translate_modules = ['all']
unaccent = False
upgrade_path =
without_demo = all
workers = 2And that's it for today. We will still need to do daily backups for our database and our filestore (located at/home/odoo/.local/share/Odoo/filestore/codingdodo_demo)
I don't have a simple strong solution to handle backups that I could quickly share into this already very long article, so I may come back and update it later.
Thanks for reading!
Now that you have your production environment ready, what are you building? Keep in touch by following me on Twitter. And please consider becoming a member for future updates ?.
For Your next projects, consider checking out these tutorials:
- Part 1 - Basic Structure of the OWL Project and Components
- OWL in Odoo 14 - How to extend and patch existing OWL Components.
- Working with Dates in Odoo - Analysis and Use Cases



